Linux comes equipped with a plethora of networking utilities to choose from. tcpdump is one such powerful networking tool that can capture and analyze network traffic should you need to troubleshoot network errors on Linux.
Let's get hands-on with the tcpdump command and explore how to use it to capture network traffic.
Installing tcpdump in Linux
tcpdump usually comes pre-installed with all mainstream Linux distributions and security-based alternatives. So you should be able to use it right away by typing in tcpdump with a sudo prefix.
In case you are unable to run the tcpdump command and are stuck at the "tcpdump: command not found" error, let's learn how to install tcpdump on your Linux machine.
To install tcpdump, fire up the terminal and run the command corresponding to the Linux distro that you're currently using:
On Debian/Ubuntu derivatives, run:
sudo apt-get install tcpdumpOn Arch-based systems, run:
sudo pacman -S tcpdump
To install the tcpdump utility on Fedora, CentOS, and RHEL, issue the following command:
sudo dnf install tcpdumpNote that if you're asked to install libcap, type in Yes or Y as it is a core dependency, without which tcpdump will refuse to start up. This should install the tcpdump utility and solve the "command not found" error.
Now that tcpdump has been installed on your system, let's explore the different options and functionalities it offers.
Capturing Network Traffic With tcpdump
tcpdump offers a lot of flags to modify its execution but it can be run as a standalone command as well. However, running tcpdump without any flags or arguments would be neglecting its full potential. It's always better to use a few flags to tweak the execution and output as necessary.
Type in this command to monitor network transmissions with tcpdump:
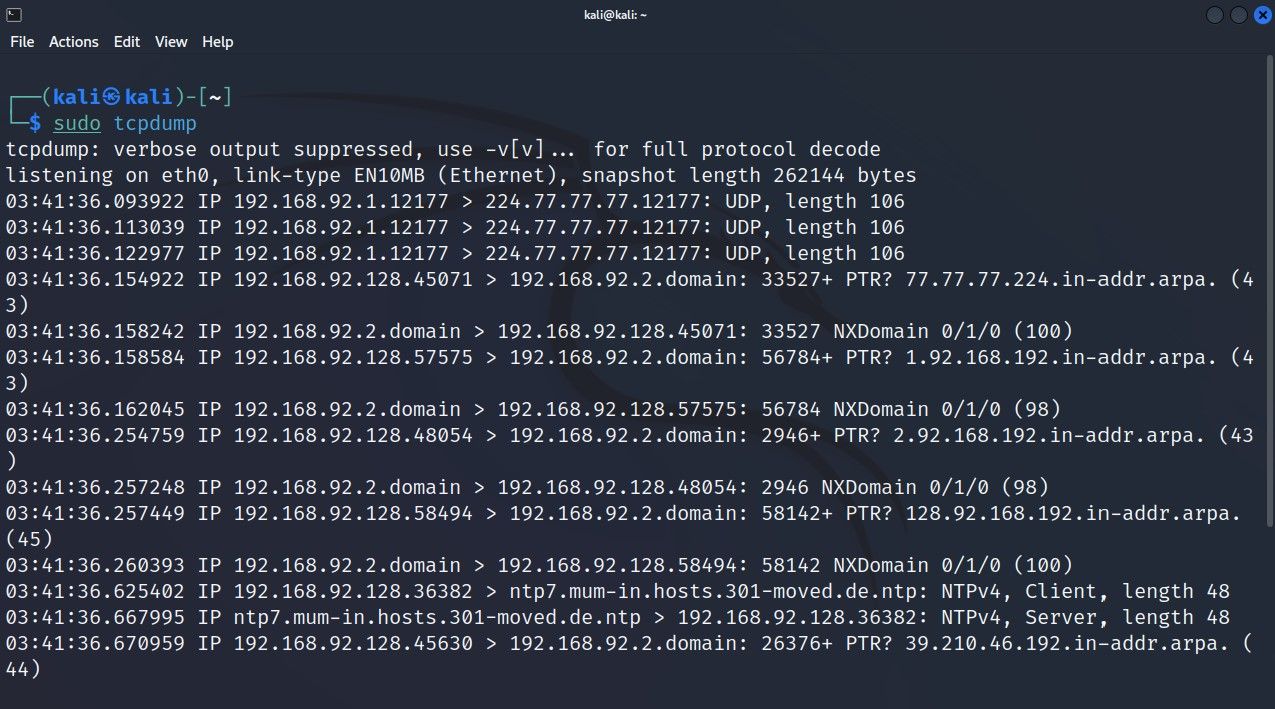
sudo tcpdumpNow tcpdump will start to automatically capture network packets until an interrupt signal is sent with Ctrl + Z to break the process manually. To limit the total number of packets captured, use the -c flag and type in the desired limit of packets next to it:
sudo tcpdump -c 5If you can't make sense of the output right now, you need to get familiar with the tcpdump output format first.
Check Available Network Interfaces With tcpdump
By default, tcpdump captures traffic from any of the available network interfaces. If you have multiple active network interfaces in use, you might want to define the network interface from which tcpdump should capture packets. To start tcpdump on a specific interface, you will have to first learn about the interface name.
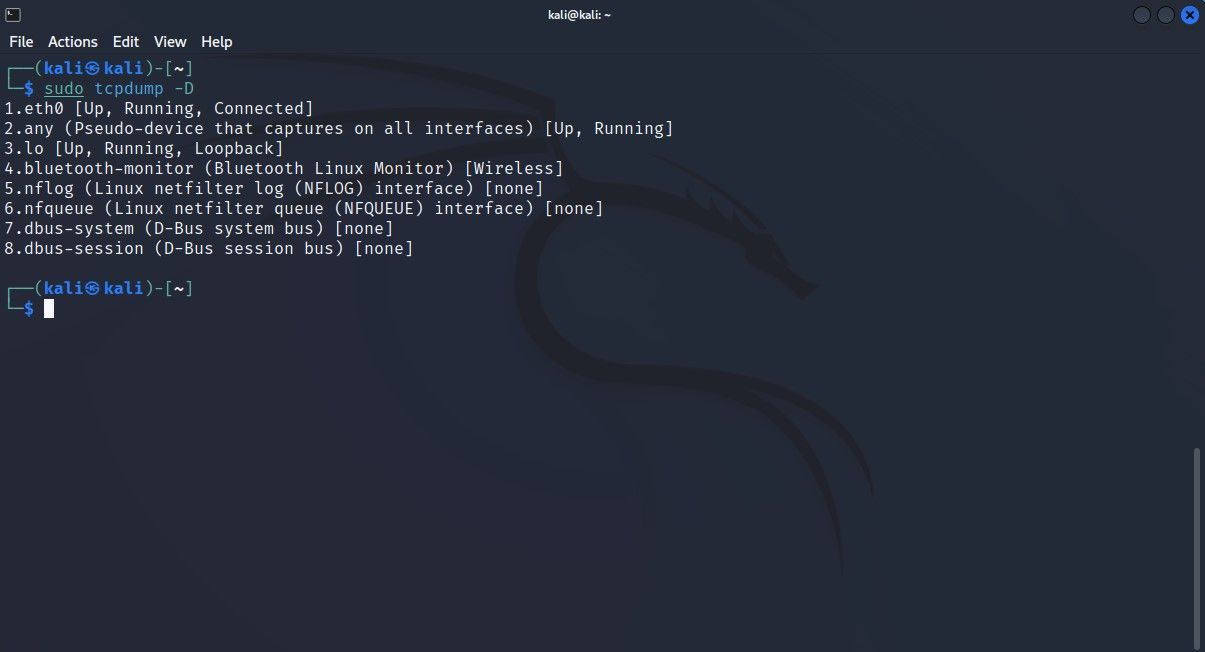
Here's how to list all available network interfaces with tcpdump:
sudo tcpdump -DOr, you can add the --list-interfaces flag to the command:
sudo tcpdump --list-interfacesThe output returned contains a list of all the active network interfaces that tcpdump can listen to. To configure tcpdump to capture transmissions from a particular network interface, type in this command:
sudo tcpdump -i interface_idOr, you can add the --interface flag to the command:
sudo tcpdump --interface interface_idNow that we have captured a few packets, let's study them closely and learn how you can tweak the output to be more readable.
Exploring tcpdump Filters
tcpdump is capable of capturing an overwhelming amount of traffic in a single run. Such information overload can throw you off track when investigating or troubleshooting issues with a specific host or network protocol.
Here's where the tcpdump filters come into play. You can append the tcpdump command with certain flags to filter out the network traffic and capture specific packets. You can then store those packets and later analyze them to get to the root of any network-related problems. Let's learn how to use filters in tcpdump.
Filter Packets Based on the Network Protocol in Use
To filter packets transmitted via a specific protocol, type in the protocol name with the tcpdump command, and it will only capture packets traveling via the defined network protocol.
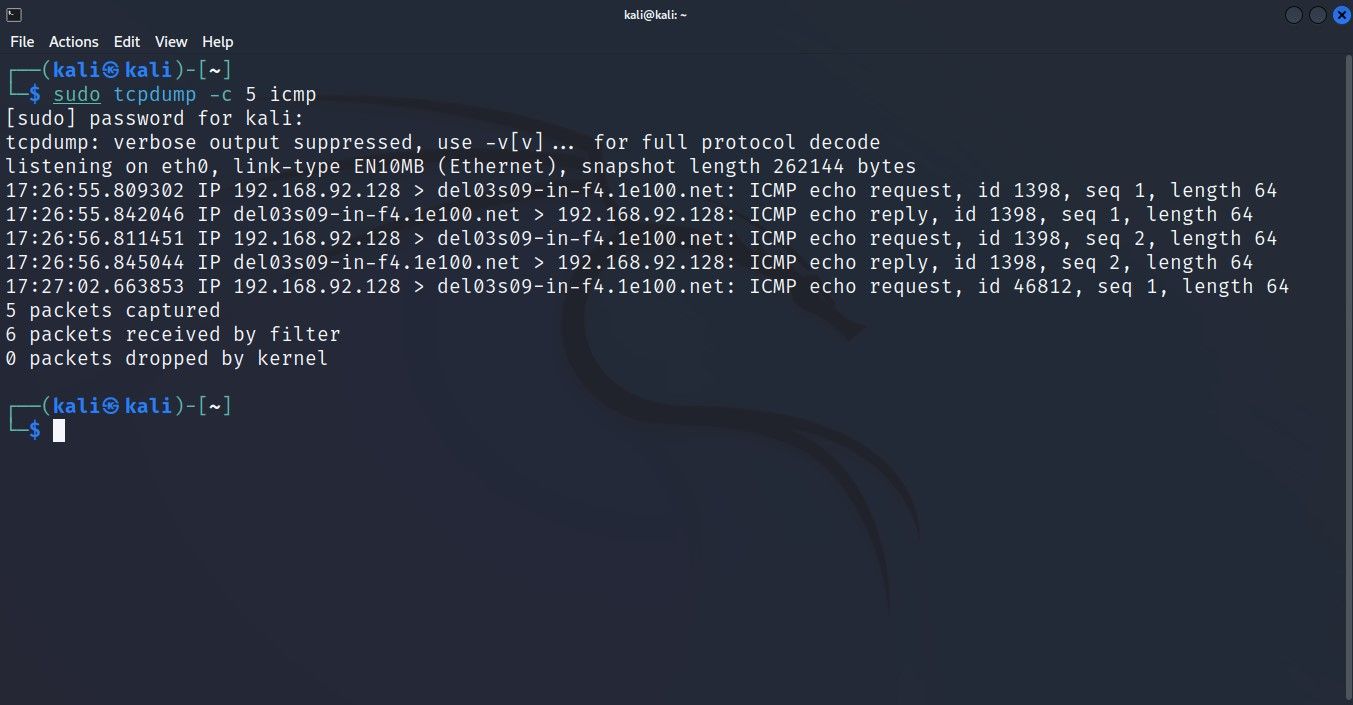
For example, to capture ICMP-based packets, you would simply attach icmp at the end of the tcpdump command. The process is the same if you wish to capture only UDP or TCP packets.
sudo tcpdump -c 5 icmpThis command will only return output if there is an exchange of data through the ICMP protocol.
Filter Packets Based on the Host
You can configure tcpdump to capture packets related to a single host with the host parameter. This is especially useful when all the systems of your network are functioning except for one. This filter lets you perform targeted investigation and speeds up the overall troubleshooting workflow since you aren't distracted by unnecessary data.
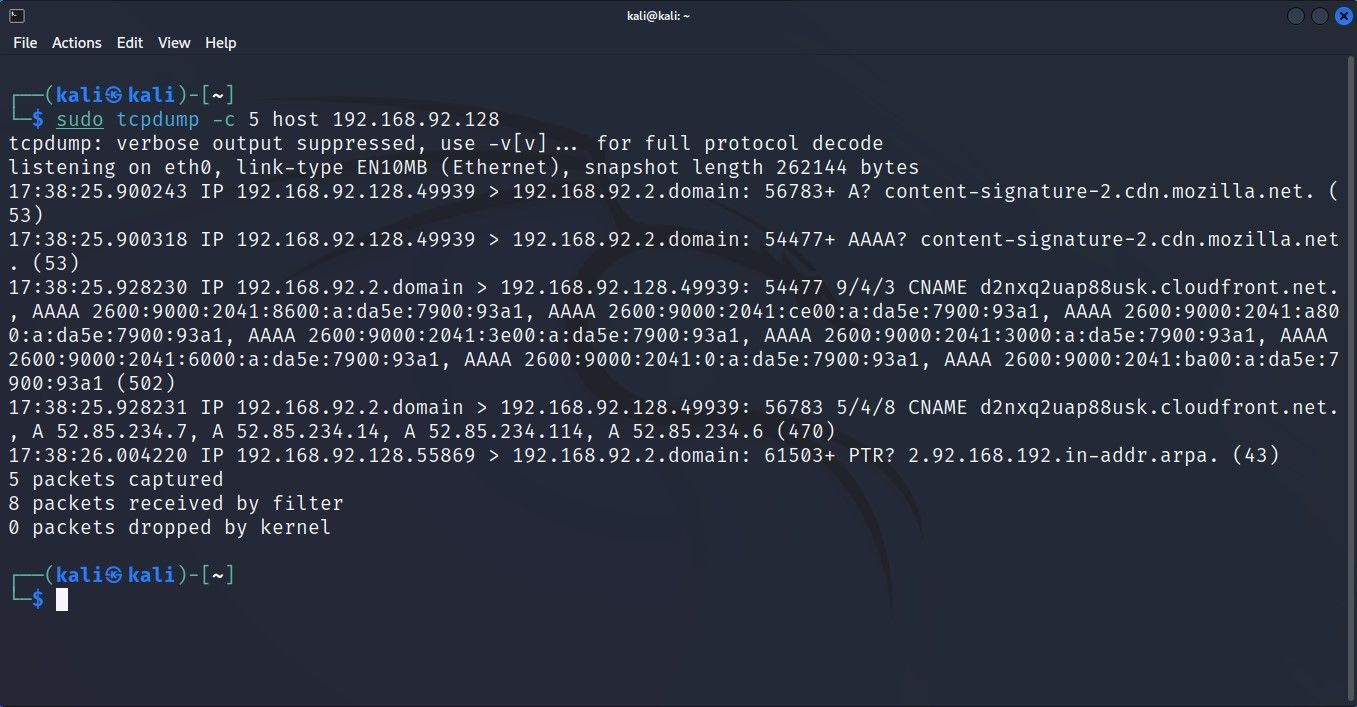
To capture packets related to a specific host, define the host's network address with the host parameter:
sudo tcpdump -c 5 host 192.168.2.1Similar to the network protocol filter, this command will only return output if any ongoing transmission is related to the defined host.
Filter Packets Based on the Active Port
tcpdump is equipped with a parameter that lets you filter network traffic and capture only packets that are transmitted to or from a specific port.
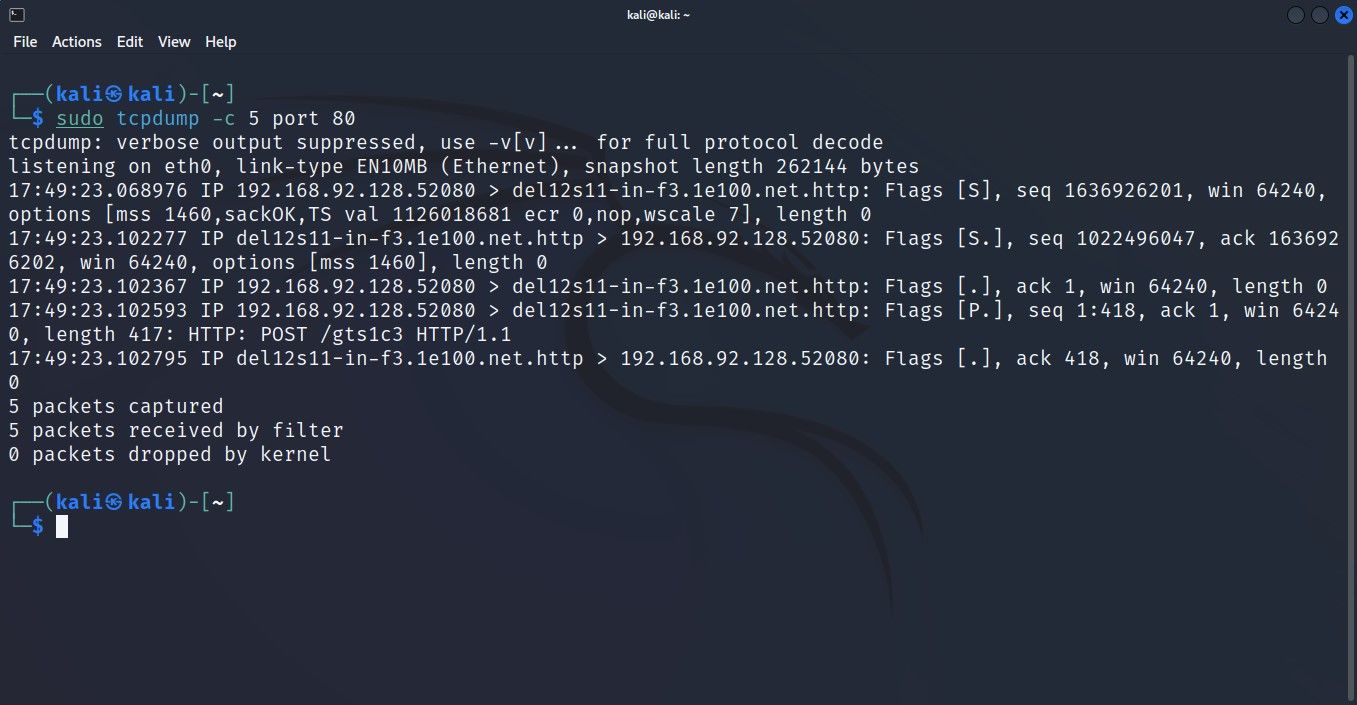
To capture packets coming from a specific port, append the port flag to the tcpdump command and define the port number next to it. For instance, to capture any incoming or outgoing HTTP traffic, define port 80:
sudo tcpdump -c 5 port 80
tcpdump will listen on port 80, waiting for HTTP transmissions. Once it detects HTTP packets in the network, it will capture them.
Combine Filters Together for Advanced Sorting
Previous sections discussed how you can filter traffic based on port, protocol, or host, but what if you wanted to capture traffic from a single port of a specific host using a particular network protocol? Well, you're in luck because this is possible, attributing to the ability to use logical operators with the tcpdump command.
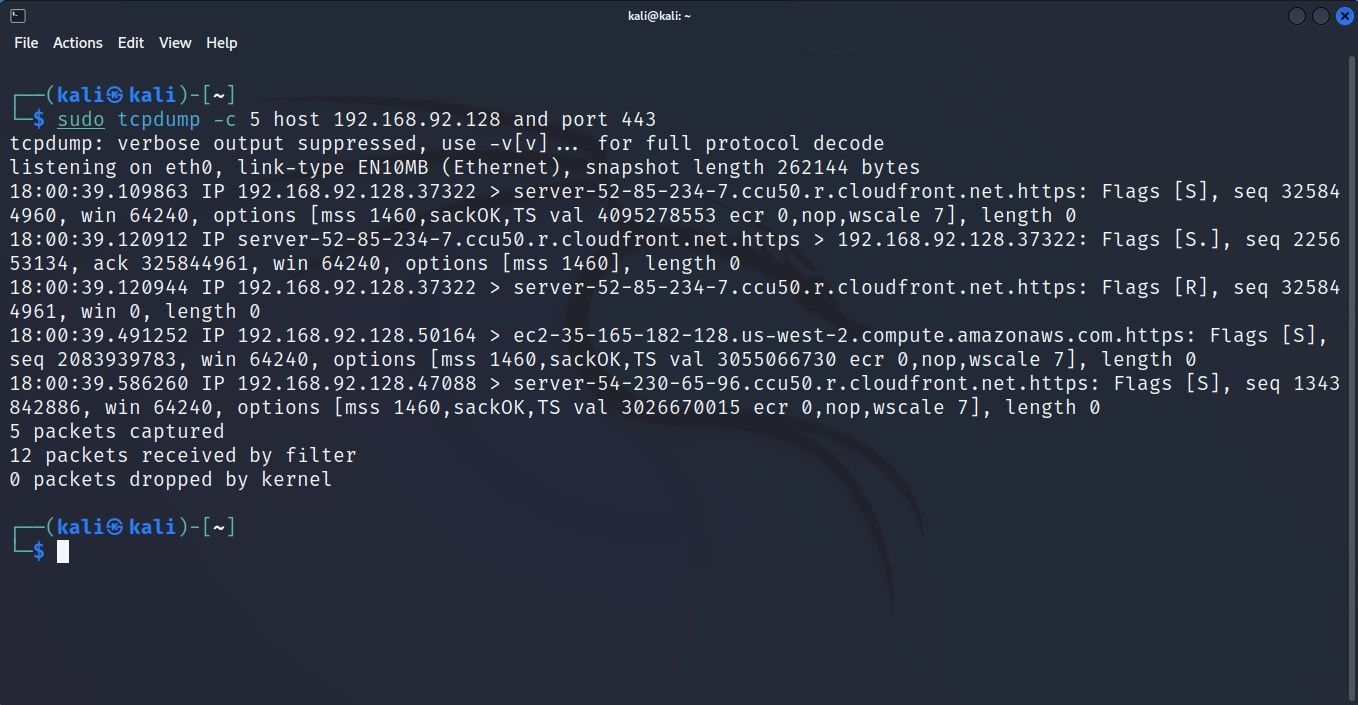
To capture packets from an individual host using port 443, use this command:
sudo tcpdump -c 5 host 192.168.2.1 and port 443
Inspect the Contents of Captured Packets
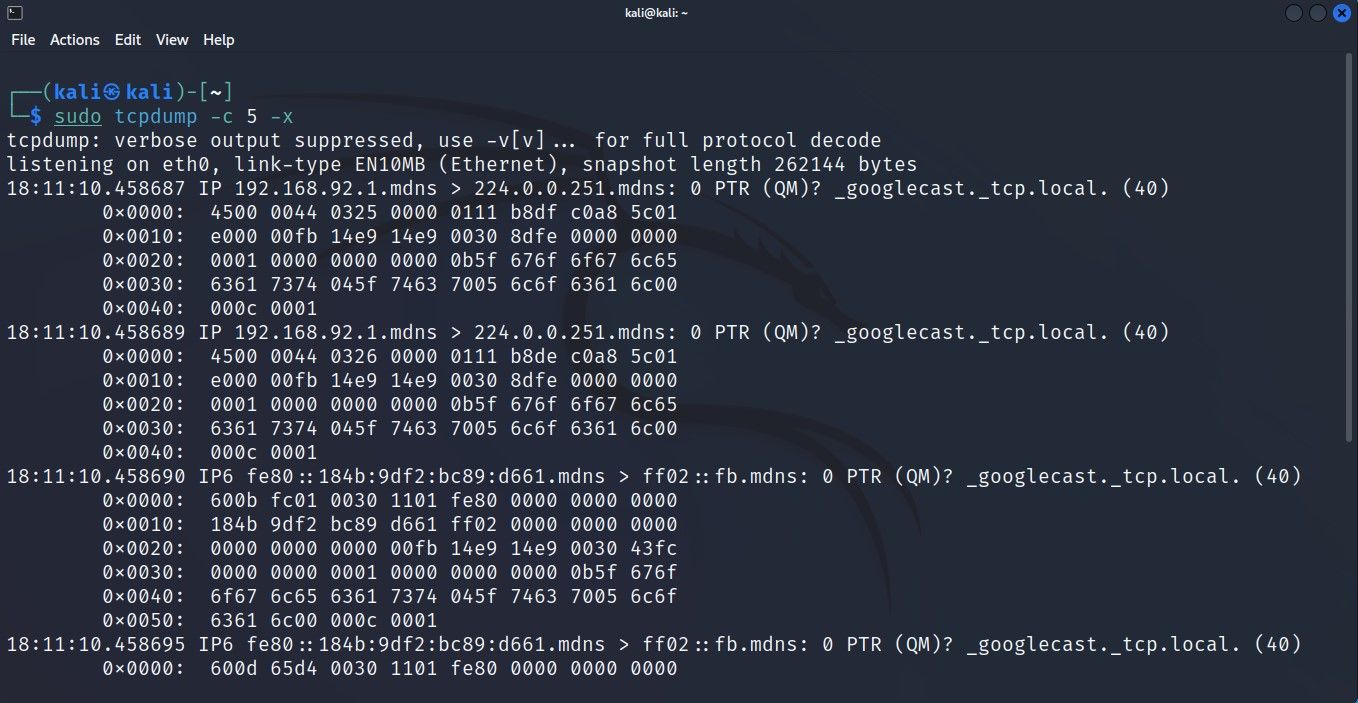
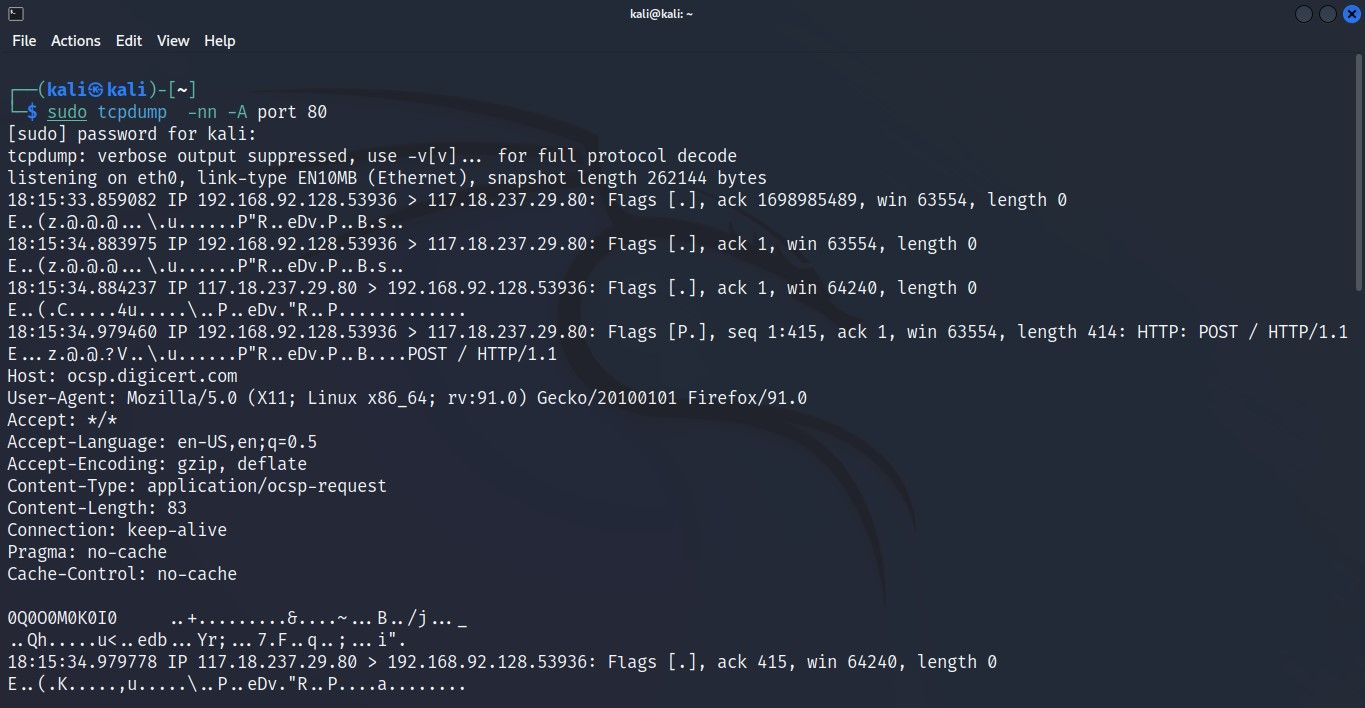
By default, tcpdump displays the headers of a packet in the output. While it is more than enough in most cases, sometimes, you might want to or need to look deeper into the captured data. You can pass certain parameters with the tcpdump command to inspect the content of the captured package.
Here's how to view the content of the packets:
sudo tcpdump -c 5 -xThis command returns the hex version of the content in a captured packet. If you wish to view the ASCII form of the data, you can pass the -A parameter with:
sudo tcpdump -ASave tcpdump Output to a File
Like almost any other Linux command-line tool, you can store the output produced by tcpdump into a file to be referenced later.
This can be done by adding the -w flag to the command. Upon execution, tcpdump will store the captured data into a .pcap file that can be later analyzed with tcpdump or other network monitoring tools like Wireshark.
Type in this command to store your tcpdump command's output into a file:
sudo tcpdump -w capture.pcapTo read a .pcap file, you can use tcpdump with the -r parameter:
sudo tcpdump -r capture.pcapLinux ships with a plethora of networking tools that can solve every network issue as long as it's on the software side of things. Knowing how to use a few of the best networking tools in Linux will definitely come in handy, whether you're a sysadmin managing networks for a living or just an everyday Linux user.
Since the actual list of available networking commands can be too much to fathom, here's a list of some of the most important Linux networking tools that you should know.
"network" - Google News
July 04, 2022 at 02:30AM
https://ift.tt/J4uqTvb
How to Capture Network Traffic in Linux With tcpdump - MUO - MakeUseOf
"network" - Google News
https://ift.tt/h4PbReN
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update

No comments:
Post a Comment